Introduction
SNOVA is a digital signature algorithm that was submitted to Round 2 of the NIST Post-Quantum Cryptography Project in February 2025. Its full name is “Simple Noncommutative-ring based UOV with key-randomness Alignment”, SNOVA is a simplified version of NOVA.
Features
The SNOVA digital signature algorithm is a variant of the UOV algorithm, retaining the UOV's
characteristic of short signatures while offering a shorter public key length compared to the
traditional UOV algorithm, thereby providing advantages in both security and efficiency aspects of
digital signatures.
Furthermore, the SNOVA algorithm provides a number of different parameter options for each security level,
including various combinations of public key and signature lengths. This feature brings greater
flexibility and adaptability to the application side, enabling SNOVA to be well-suited for diverse
scenarios, whether it be resource-constrained devices or applications requiring high-security
protection, as it allows for the selection of parameter configurations that best suit the specific
use case.
Description of SNOVA
Let \( v, o \) be positive integers with \(v>o\) and \(\mathbb{F}_{q}\) be of characteristic 2. We choose \(\mathbb{F}_{q}=\rm{GF}(16)\) for our implementation. Let \(n=v+o\) and \(m=o\). The construction of a \((v,o,q,l)\) SNOVA scheme is based on the subfield \(\boldsymbol{\mathbb{F}_{q}[S]}\).
Subring \(\boldsymbol{\mathbb{F}_{q}[S]}\) and elements in \(\boldsymbol{\mathbb{F}_{q}[S]}\).
Let \(S\) be a \(l \times l\) symmetric matrix with an irreducible characteristic polynomial. The subring \(\mathbb{F}_{q}[S]\) of \(\mathcal{R}\) is defined as \[ \mathbb{F}_{q}[S]=\{a_{0}+a_{1}S+\cdots+a_{l-1}S^{l-1}\mid a_{0},a_{1},\cdots,a_{l-1} \in \mathbb{F}_{q}\}. \] As the characteristic polynomial of \(S\) is irreducible, \(\mathbb{F}_{q}[S]\) is a field. Thus, the elements in \(\mathbb{F}_{q}[S]\) are symmetric and they all commute. Let \[ \Omega=\{(j,k):1 \le j,k \le n\} \setminus \{(j,k):v+1 \le j,k \le n\}. \] This index set \(\Omega\) is defined by the Oil-Vinegar structure.
Central map of SNOVA.
For \(i \in \{1,\ldots,m\}\), we define \[ \left[ F_{i}\right]= \begin{bmatrix} F_{i,jk} \end{bmatrix} = \begin{bmatrix} F_{i}^{11} & F_{i}^{12} \\ F_{i}^{21} & 0 \end{bmatrix} \] where \(F_{i}^{11}\), \(F_{i}^{12}\) and \(F_{i}^{21}\) are matrices over \(\mathcal{R}\) randomly generated of size \(v \times v\), \(v \times o\) and \(o \times v\), respectively. We use random matrices and \(\left[F_{1}\right],\ldots,\left[F_{m}\right]\) to construct the central map. First, we randomly choose invertible elements \(A_{i,\alpha}\) and \(B_{i,\alpha}\) from \(\mathcal{R}\), and invertible elements \(Q_{i,\alpha,1}\) and \(Q_{i,\alpha,2}\) from \(\mathbb{F}_{q}[S]\). The central map of SNOVA scheme is \(\widetilde{F}=\left[\widetilde{F}_{1},\cdots,\widetilde{F}_{m}\right]:\mathcal{R}^{n} \rightarrow \mathcal{R}^{m}\), for \(i \in \{1,\cdots,m\}\), \(\widetilde{F}_{i}\) is defined to be \[ \widetilde{F}_{i}(X_{1},\ldots,X_{n})=\sum\limits_{\alpha=0}^{l^{2}+l-1}A_{i,\alpha} \cdot \left( \sum\limits_{(j,k) \in \Omega } X_{j}^{t}\left(Q_{i,\alpha,1}F_{i^{\prime},jk}Q_{i,\alpha, 2}\right)X_{k}\right) \cdot B_{i,\alpha} \] where \(i^{\prime} = (i+ \alpha) \mod m\) and \(F_{i^{\prime},jk}\) is the \((j,k)\)-th entry of \(\left[F_{i^{\prime}}\right]\). Changes to the Round 1 central map are: the sum over \(\alpha\) has been extended from \(l^2\) to \(l^{2}+l\) elements, the \(ABQ\) matrices now depend not only on \(\alpha\) but also on \(i\), and \(F_{i^\prime}\) depends on both \(i\) and \(\alpha\).
Invertible linear map.
The invertible linear map in SNOVA scheme is the map \(T: \mathcal{R}^{n} \rightarrow \mathcal{R}^{n}\) corresponding to the matrix \[ \left[T \right]= \left[T_{ij} \right]= \begin{bmatrix} I^{11} & T^{12}\\ 0 & I^{22}\\ \end{bmatrix}, \] where \(T^{12}\) is a \(v \times o\) matrix consisting of nonzero entries \(T_{ij}\) chosen randomly in \(\mathbb{F}_{q}[S]\). Note that \(T_{ij}\) is symmetric and commutes with other elements in \(\mathbb{F}_{q}[S]\). In particular, \(T_{ij}\) commutes with \(Q_{i,\alpha,1}\) and \(Q_{i,\alpha,2}\). The matrices \(I^{11}\) and \(I^{22}\) are identity matrices over \(\mathcal{R}\). Therefore, \(\left[T \right]\) is invertible and hence \(T\). Note that since \(\mathbb{F}_{q}\) is of characteristic \(2\), the matrix \(\left[T^{-1} \right]=\left[T \right]\).
Public map.
We construct the public key \(\left[ P_{1}\right],\ldots,\left[ P_{m}\right]\) via the congruence relation \[ \left[ P_{1}\right]= \begin{bmatrix} P_{1,j,k} \end{bmatrix} = \left[T \right]^{t}\left[ F_{1}\right]\left[T \right],\ldots, \left[ P_{m}\right]= \begin{bmatrix} P_{m,j,k} \end{bmatrix} = \left[T \right]^{t}\left[ F_{m}\right]\left[T \right]. \] The public map of SNOVA is \(\widetilde{P} = \widetilde{F} \circ T\). For \(i\in \{1,2,\dots,m\}\), \(\widetilde{P}_{i}=\widetilde{F}_{i} \circ T\). Then, by the relation \({\mathbf{X}}=\left[T \right] \cdot {\mathbf{U}}\) where \({\mathbf{U}}=(U_{1},\cdots,U_{n}) \in \mathcal{R}^{n}\) and the commutativity of \(\mathbb{F}_{q}[S]\), we have that \[ \widetilde{P}_{i}({\mathbf{U}})=\widetilde{F}_{i}(T({\mathbf{U}}))=\sum\limits_{\alpha=0}^{l^{2}+l-1} \sum\limits_{j=1}^{n}\sum\limits_{k=1}^{n}A_{i,\alpha} \cdot U_{j}^{t}(Q_{i,\alpha,1}P_{i^{\prime},jk}Q_{i,\alpha,2})U_{k} \cdot B_{i,\alpha} \] where \(i^{\prime}=(i +\alpha) \mod m\) and \(P_{i^{\prime},jk}\) is the \((j,k)\)-th entry of matrix \(\left[P_{i^{\prime}}\right]\). By introducing the matrices \(A_{i,\alpha},B_{i,\alpha},Q_{i,\alpha,1},Q_{i,\alpha,2}\), the public map \(\widetilde{P}\) is not a sparse UOV map when we regard it as over \(\mathbb{F}_{q}\).
Public key of SNOVA.
The public key are the matrices \(\left[P_{i} \right]\) and the matrices \(A_{i,\alpha}\), \(B_{i,\alpha}\), \(Q_{i,\alpha, 1}\) and \(Q_{i,\alpha, 2}\) for \(\alpha = 0,1,\dots,l^{2}+l-1\), or simply the seed \(\bf{s}_{public}\) which generates them.By utilizing matrices \(\left[P_{i} \right]\) and the seed \(\bf{s}_{public}\), the verifier is capable to obtain the public map \(\widetilde{P}\) and subsequently verify the received signature. We propose parameter settings aiming for NIST security levels I, III, and V. For security level I, our \(l=4\) parameter set results in a public key size of \(1016\) bytes and a signature size of \(248\) bytes. With these performances, we believe that the SNOVA scheme has strong competitiveness compared to other post-quantum signature schemes.
Parameters
| SL | (v, o, q, l) | public key size | sign size | private key size (esk) | private key size (ssk) |
|---|---|---|---|---|---|
| I | (37, 17, 16, 2) | 9842 | 124 | 91440 | 48 |
| (25, 8, 16, 3) | 2320 | 164.5 | 39576 | ||
| (24, 5, 16, 4) | 1016 | 248 | 36848 | ||
| III | (56, 25, 16, 2) | 31266 | 178 | 300848 | |
| (49, 11, 16, 3) | 6005.5 | 286 | 177060 | ||
| (37, 8, 16, 4) | 4112 | 376 | 133040 | ||
| (24, 5, 16, 5) | 1578.5 | 378.5 | 60048 | ||
| V | (75, 33, 16, 2) | 71890 | 232 | 704532 | |
| (66, 15, 16, 3) | 15203.5 | 380.5 | 435423 | ||
| (60, 10, 16, 4) | 8016 | 576 | 395248 | ||
| (29, 6, 16, 5) | 2716 | 453.5 | 100398 |
Table of key-sizes and lengths of the signature of SNOVA parameter settings. (bytes)
Security & Sizes
During Round 1 of the NIST competition severeal new attacks were described. In the table below we mention the security against the best known attack as of February 2025. Refer to the Round 2 Supporting Document for security estimates for other attacks.
| Security in log #gates and sizes | ||||||||
| SL | (v, o, q, l) | Best Attack | pk(Bytes) | sig(Bytes) | ||||
| I | (37, 17, 16, 2) | 153 | 9842 | 124 | ||||
| (25, 8, 16, 3) | 166 | 2320 | 164.5 | |||||
| (24, 5, 16, 4) | 180 | 1016 | 248 | |||||
| III | (56, 25, 16, 2) | 221 | 31266 | 178 | ||||
| (49, 11, 16, 3) | 220 | 6005.5 | 286 | |||||
| (37, 8, 16, 4) | 279 | 4112 | 376 | |||||
| (24, 5, 16, 5) | 257 | 1578.5 | 378.5 | |||||
| V | (75, 33, 16, 2) | 287 | 71890 | 232 | ||||
| (66, 15, 16, 3) | 293 | 15203.5 | 380.5 | |||||
| (60, 10, 16, 4) | 343 | 8016 | 576 | |||||
| (29, 6, 16, 5) | 310 | 2716 | 453.5 | |||||
Comparison
A comparison of the key and signature sizes of SNOVA, and the key and signature sizes of the NISTPQC finalists (SPHINCS+, DILITHIUM and Falcon), Pre-Quantum (RSA and EdDSA) and compressed UOV.
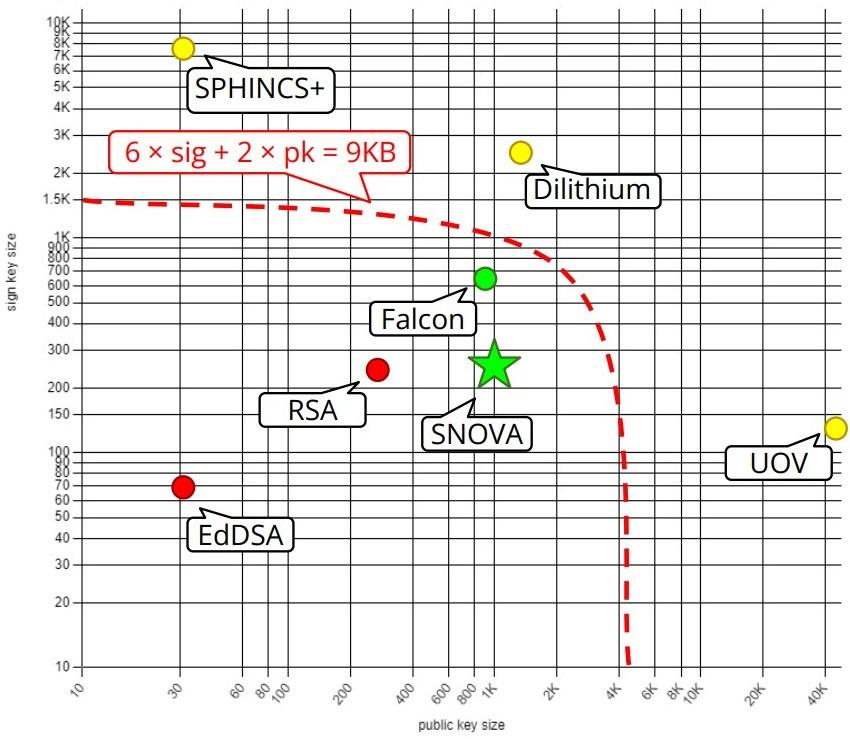
Making Internet post-quantum. For easily upgrading existing protocols (e.g. TLS) to become quantum-resistant, the article of CloudFlare gives the condition: 6 x signature + 2 x pk ≤ 9KB.
Performance
Benchmark results on a modern desktop system (Arrow Lake) using AVX2 instructions. ESK: Expanded Secret Key, SSK: Seeded Secret Key (always 48 bytes). The verify expands the public key.
| SL | (v,o,l) | XOF | Gen cycles | Sign cycles SSK | Sign cycles ESK | Verify cycles |
| I | (37, 17, 16, 2) | AES | 754,677 | 737,085 | 262,422 | 151,842 |
| (37, 17, 16, 2) | SHAKE | 923,342 | 905,717 | 259,619 | 317,564 | |
| (25, 8, 16, 3) | AES | 246,298 | 494,904 | 340,740 | 176,153 | |
| (25, 8, 16, 3) | SHAKE | 317,078 | 563,468 | 346,892 | 244,364 | |
| (24, 5, 16, 4) | AES | 222,876 | 530,409 | 385,429 | 205,829 | |
| (24, 5, 16, 4) | SHAKE | 286,892 | 594,690 | 385,965 | 268,342 | |
| III | (56, 25, 16, 2) | AES | 3,289,256 | 2,876,627 | 648,245 | 531,159 |
| (56, 25, 16, 2) | SHAKE | 3,829,031 | 3,424,697 | 651,370 | 1,079,757 | |
| (49, 11, 16, 3) | AES | 1,503,852 | 2,061,825 | 984,405 | 675,680 | |
| (49, 11, 16, 3) | SHAKE | 1,839,992 | 2,390,210 | 997,315 | 987,091 | |
| (37, 8, 16, 4) | AES | 1,039,795 | 1,804,955 | 1,102,301 | 652,463 | |
| (37, 8, 16, 4) | SHAKE | 1,263,702 | 2,030,093 | 1,100,166 | 889,065 | |
| (24, 5, 16, 5) | AES | 456,998 | 1,421,115 | 1,120,762 | 685,307 | |
| (24, 5, 16, 5) | SHAKE | 553,744 | 1,524,408 | 1,128,682 | 787,049 | |
| V | (75, 33, 16, 2) | AES | 9,745,037 | 8,052,855 | 1,426,465 | 1,309,034 |
| (75, 33, 16, 2) | SHAKE | 11,034,489 | 9,328,179 | 1,450,322 | 2,595,930 | |
| (66, 15, 16, 3) | AES | 4,561,008 | 5,700,004 | 2,215,902 | 1,737,533 | |
| (66, 15, 16, 3) | SHAKE | 5,376,257 | 6,516,854 | 2,223,800 | 2,567,815 | |
| (60, 10, 16, 4) | AES | 3,519,404 | 5,574,943 | 2,800,653 | 1,932,041 | |
| (60, 10, 16, 4) | SHAKE | 4,244,420 | 6,216,789 | 2,819,456 | 2,648,472 | |
| (29, 6, 16, 5) | AES | 804,402 | 2,278,333 | 1,758,416 | 1,073,040 | |
| (29, 6, 16, 5) | SHAKE | 985,666 | 2,442,798 | 1,757,620 | 1,249,950 |
These achievements indicate significant prospects for the application of SNOVA in most scenarios.